This blog is planned as a primer on the classification of cryptographic keys utilised for securing digital applications and encrypted messages.
Introduction
Just as there are home keys for the automobile, front door, garage, etc., cryptographic legends can do many other purposes. Comprehending these keys necessitates an understanding of their type, i.e. the different kinds of key and their effects and processes.
At its simplest level, a cryptographic legend is just a lucky line consisting of hundreds or thousands of ones and zeroes (aka binary digits,). Nevertheless, keys are always created for a distinct function, and the linked key meta-data defines the effects of the key.
The distinction between symmetric and asymmetric keys
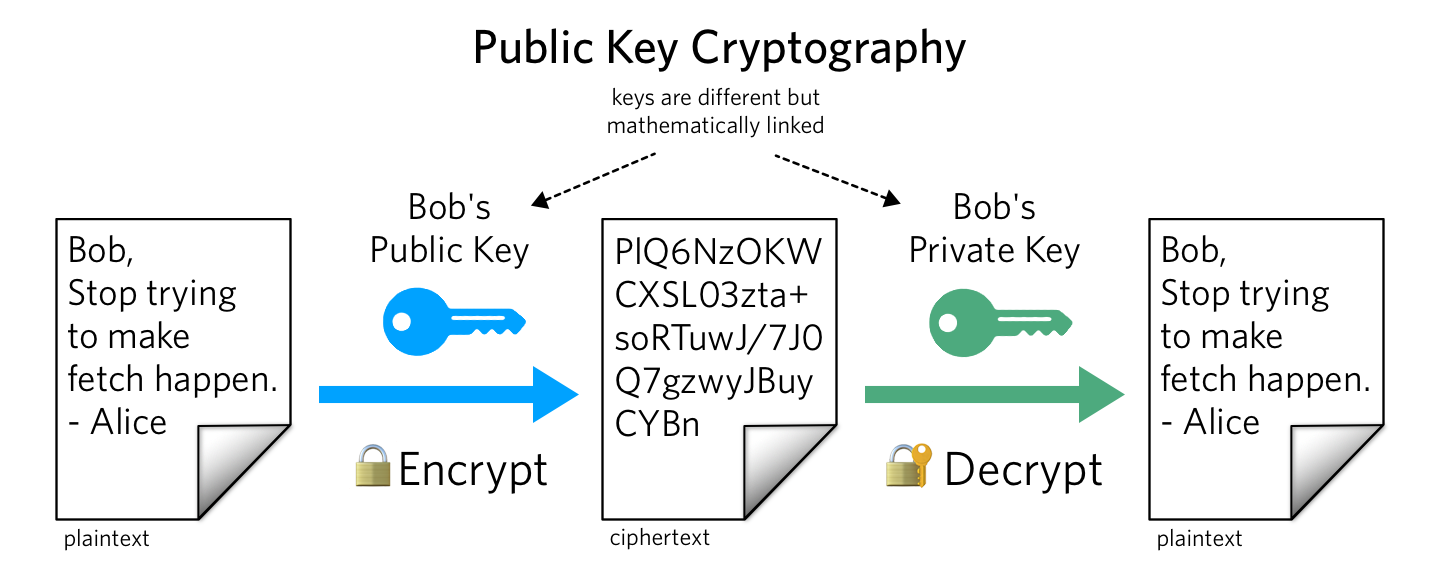
Firstly, and most notably, there are two direct types of cryptographic keys: symmetric and asymmetric. The latter still come in mathematically-related teams consisting of a private key and a public key. The protection of cryptographic applications critically relies on symmetric keys and secret keys always being held secret, whilst public keys (as their name implies) are not private.
The distinction between symmetric and asymmetric legends is best illustrated using the model of encrypting a statement to defend its confidentiality. Symmetric key encryption algorithms employ a single symmetric legend for both encryption and decryption, whereas asymmetric key encryption programs (aka public key algorithms) operate two separate but connected keys for encryption and decryption.
Symmetric algorithms have the edge in that they are much shorter than asymmetric algorithms, and can take thousands of legends with very little computing overhead. Nevertheless, the drawback is that a symmetric key must be kept secret, and yet has to be sent to the receiving end, which suggests there is a chance of it being blocked and operated by gossip to illicitly decrypt the message.
Of course, this can be overcome by utilising a key agreement protocol such as Diffie Hellman, but another system for short messages or low-bandwidth transmission is to use an asymmetric algorithm. Here, the sender can encrypt the transmission with the planned recipient’s public key and the recipient can utilise their corresponding secret key to decrypt it. Anyone blocking the encrypted messages will just see arbitrary data; only the planned recipient with the right private key can decrypt the transmission. While the public key can be freely shared with anyone, the intended recipient must support the private key unknown.
Static vs temporary keys and crypto-period
Cryptographic legends may be either fixed (prepared for long term usage) or temporary (scheduled to be used only for a single session or transaction). The crypto-period (i.e. lifetime) of fixed legends may vary from days to weeks, months or even years relying on what they are used for. In broad, the more a key is used, the easier it is to shoot and the more information is at threat should it be exposed, so it is crucial to provide keys are returned when required (this procedure is called updating or cycling).
Conclusion: Encrypted messages are a good way to keep your data private and secret so that intruders cannot enter easily.